September 29, 2025
Effortless Vulnerability Management.
Intelligent Insights. Real Security.
Discover, manage, and remediate vulnerabilities across your organisation - all from a single, collaborative platform.
Discover, manage, and remediate vulnerabilities across your organisation - all from a single, collaborative platform.


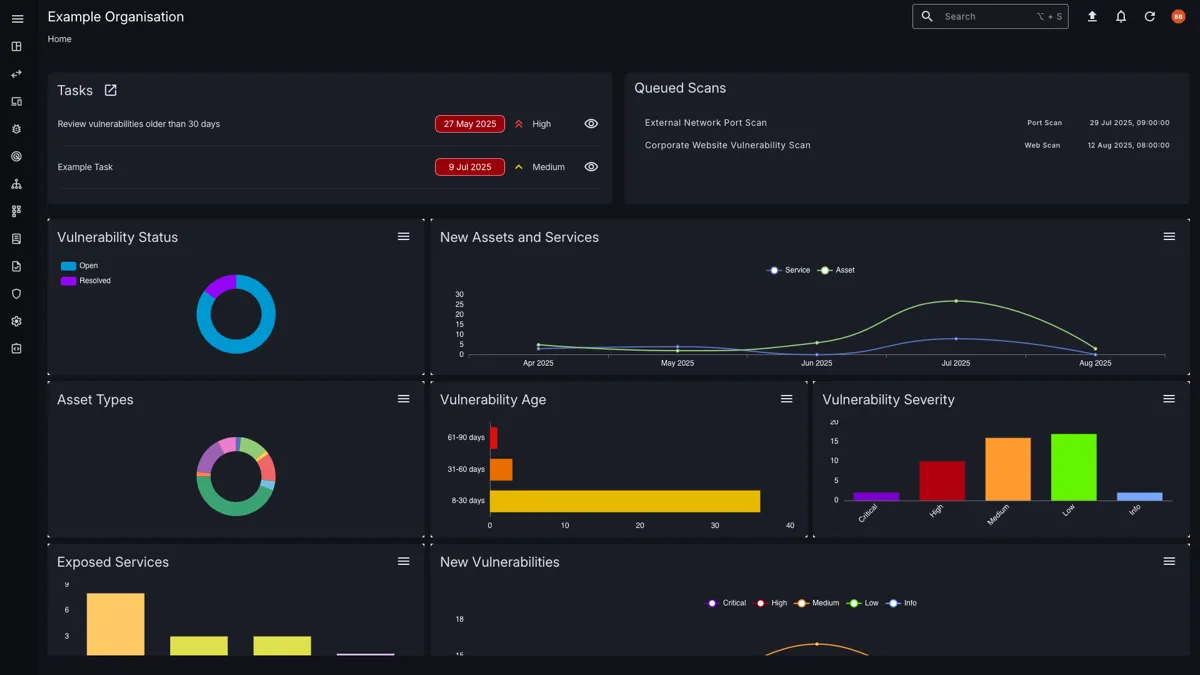
The Attack Surface Center is a platform designed to help organisations manage their security workflows, automate vulnerability scanning, and build professional penetration testing reports. It is ideal for security teams looking to collaborate on security assessments, manage vulnerabilities, and streamline their penetration testing processes.
With the Attack Surface Center, you can easily discover and manage your attack surface, track vulnerabilities, and generate comprehensive reports to share with stakeholders. The platform is user-friendly and intuitive, making it easy for security teams of all levels to use.
Whether you're a small business or a large enterprise, the Attack Surface Center provides the tools you need to stay ahead of cyber threats and protect your organisation's assets.
Attack Chains is a powerful tool that helps you to visualise and understand the attack chain of your application. It provides an overview of the vulnerabilities and their impact on your systems, applications, and networks.
With Attack Chains you can visually see the route taken to a compromise. During the remediation phase you will be able to see the impact of your changes in real-time and how they affect the cyber kill chain.

Integrate with AWS to automatically discover and manage your cloud assets, ensuring visibility and control over your attack surface.

Connect your GitHub repositories to track vulnerabilities in your codebase and manage security issues directly from the platform.

Receive real-time notifications and alerts in Slack, keeping your team informed about vulnerabilities and security issues as they arise.
Attack Surface Center’s asset management feature allows you to easily manage your assets, track their status, and identify vulnerabilities. It provides an overview of your assets and their vulnerabilities, making it easy to prioritise remediation efforts.
Our Asset Management functionality supports Domains, IP Addresses, Hostnames / Subdomains, Email addresses, and Cloud Storage containers.
Filtering and searching is easy. See the information you want with customisable column views.
Attack Surface Center’s vulnerability scanning feature allows you to scan your assets for vulnerabilities. Configure your scans to run automatically at a schedule that suits you.
See the results of your scans and their history. Quickly navigate to the discovered assets and vulnerabilities with a click of a button.
The Attack Surface Center is a powerful Attack Surface Management (ASM) platform that helps you discover, manage, and secure your attack surface.
With features like asset discovery, risk management, and vulnerability scanning, the Attack Surface Center provides you with the tools you need to protect your organisation from cyber threats.
Our ethical hacking pentesting services can help you to identify and mitigate security vulnerabilities in your applications, infrastructure, and networks. Our UK-wide pentest coverage ensures your business stays secure, compliant, and resilient against evolving threats.
Each of our services comes with complimentary access to our attack surface management platform, allowing you to leverage its powerful features alongside our expert security assessments.
See our full list of cybersecurity services for more information, or get in touch to discuss your specific needs.
Contact us to discuss your testing requirements or to schedule a penetration test with our UK based cyber security team.
Stay informed with expert analysis and in-depth coverage of the latest news, trends, innovations, and insights in cybersecurity. Whether you're a business, or an individual, our articles aim to offer valuable knowledge to enhance your understanding of cybersecurity and its impact.

DKIM is an email authentication method for a domain to sign its emails with a cryptographic signature to allow recipients to verify that the email authenticity.

DMARC is an important requirement for email security to help your business improve email deliverability and protect against phishing and spoofing attacks.
Prevent email spoofing and phishing attacks with SPF (Sender Policy Framework). Implement SPF to enhance your email security and protect your domain reputation.