Asset Management Feature
Discover, Monitor, and Secure Your Assets
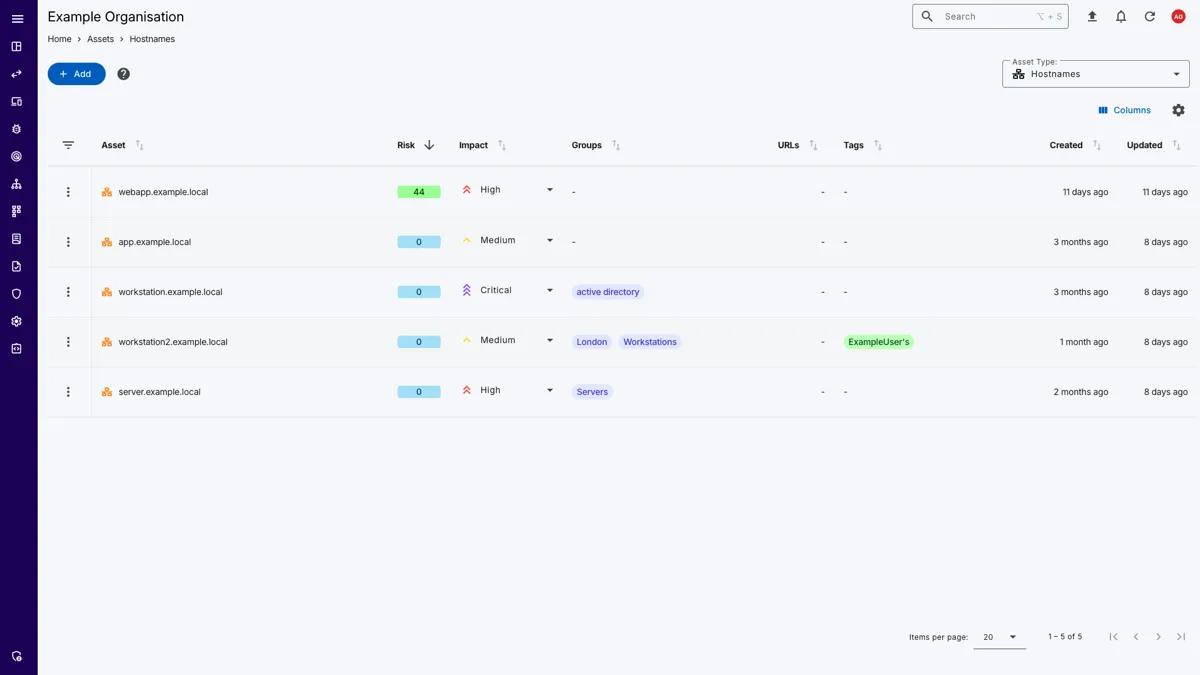

Easily create and manage assets with detailed information about each asset, its impact on your organisation, and assign them to groups for easier management.
You can easily select the type of asset you want to create, such as a hostname, domain, or IP address.
The Assets page provides a view of all assets across your organisation. You can filter and sort assets by various criteria, such as type, group, and risk score, to easily identify high-value assets and potential risks.
View individual asset details, including associated vulnerabilities, risk scores, and contextual information.
Quickly manage your organisational assets, understand the security posture of each asset and make informed decisions about remediation efforts.
Gain actionable insights into your security operations with the asset inventory, enabling you to track vulnerabilities and prioritise remediation efforts based on the criticality of each asset.
Easily identify high-value assets, track vulnerabilities associated with specific assets, and prioritise remediation efforts based on the criticality of each asset.
The risk scoring system provides a clear understanding of the potential impact of your assets, allowing you to focus on the most critical issues first.
Risk scores are calculated based on various factors, including severity, impact, maximum severity, and maximum impact.
With this information we provide a normalised risk score that is easy to understand and prioritise. This risk score includes all vulnerabilities associated with each asset.
Attack Surface Center provides automated asset discovery capabilities through DNS, WHOIS, and other sources, allowing you to quickly identify and import assets from various sources. This includes network devices, servers, applications, and cloud resources. By automating asset discovery, you can ensure that your asset inventory is always up-to-date and accurate.
This feature allows you to gather additional information about your assets without actively probing them, providing a more complete view of your infrastructure.
Sign up to the Attack Surface Center today and experience the benefits of streamlined asset management and enhanced security operations.Ready to take control of your asset management?