Attack Chain Mapping
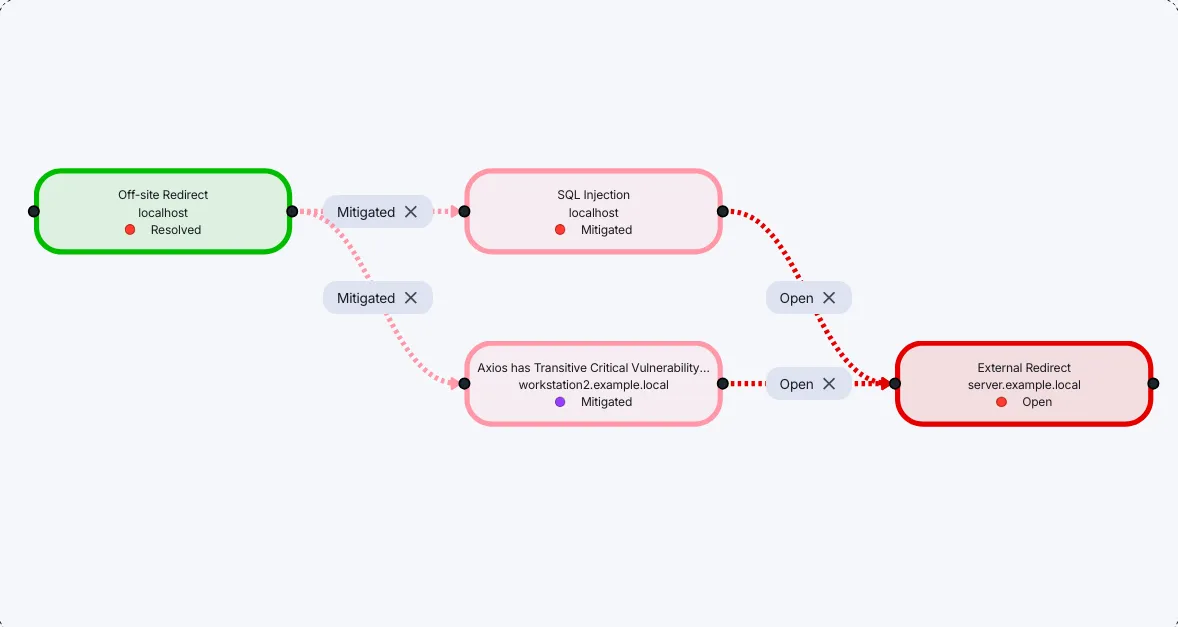
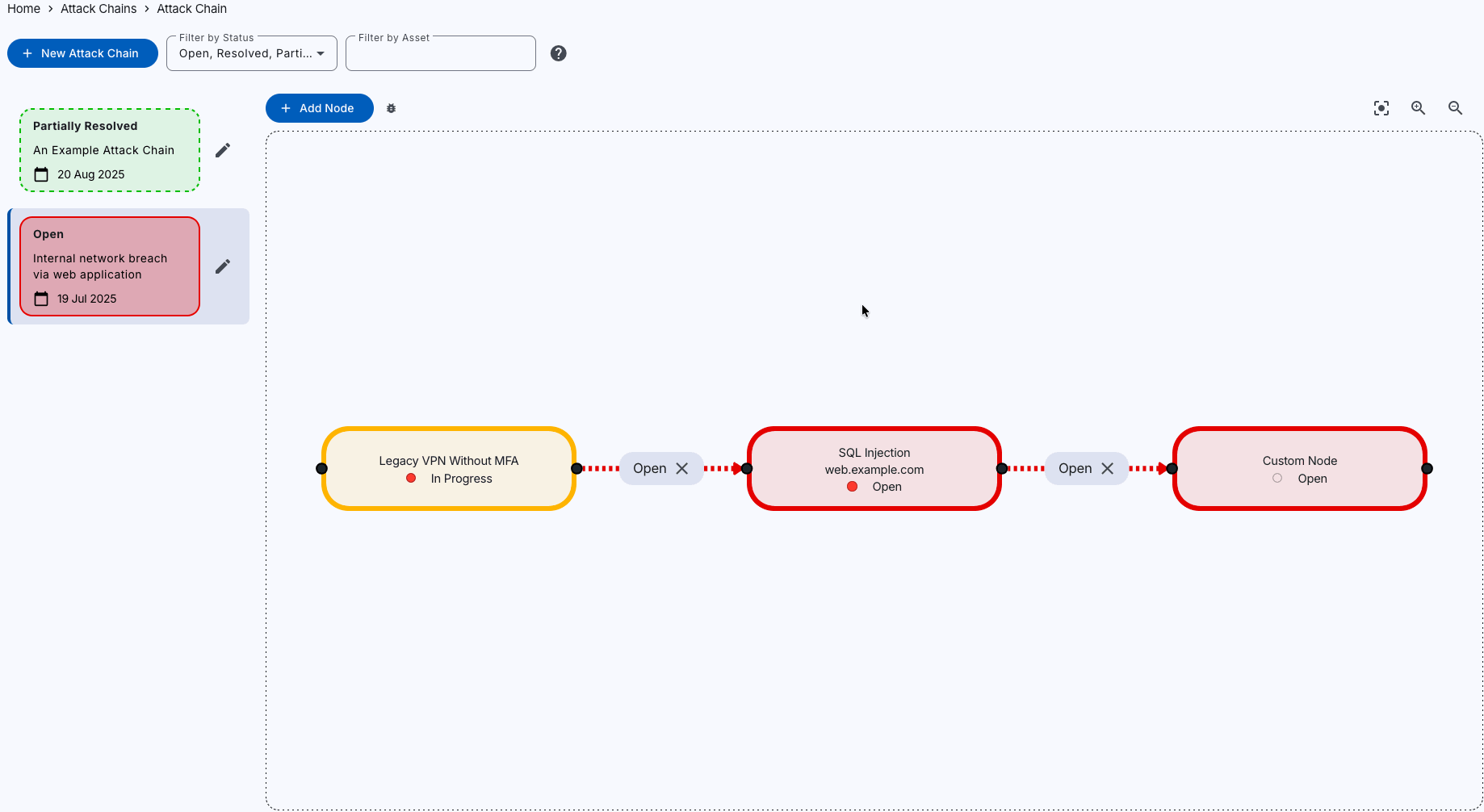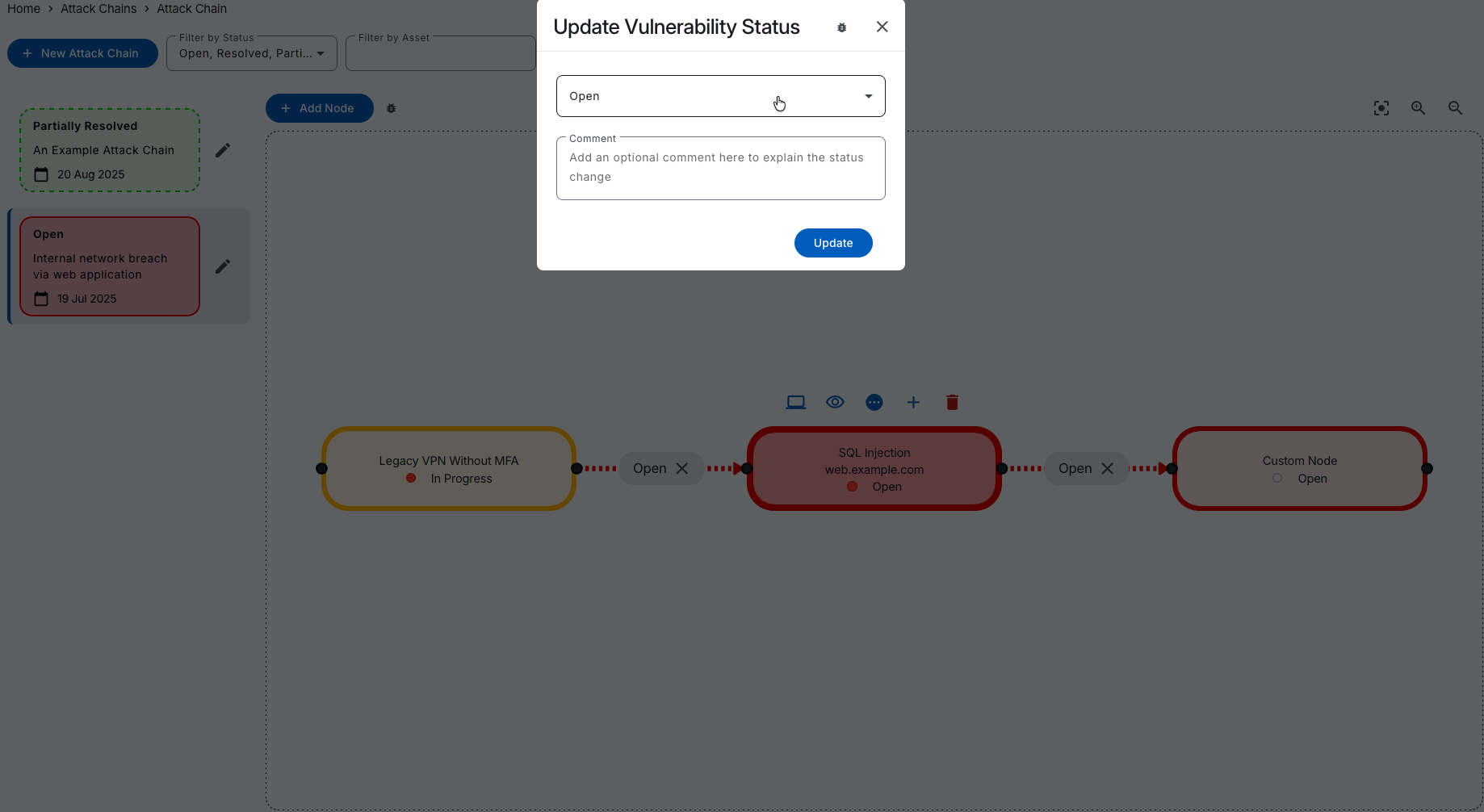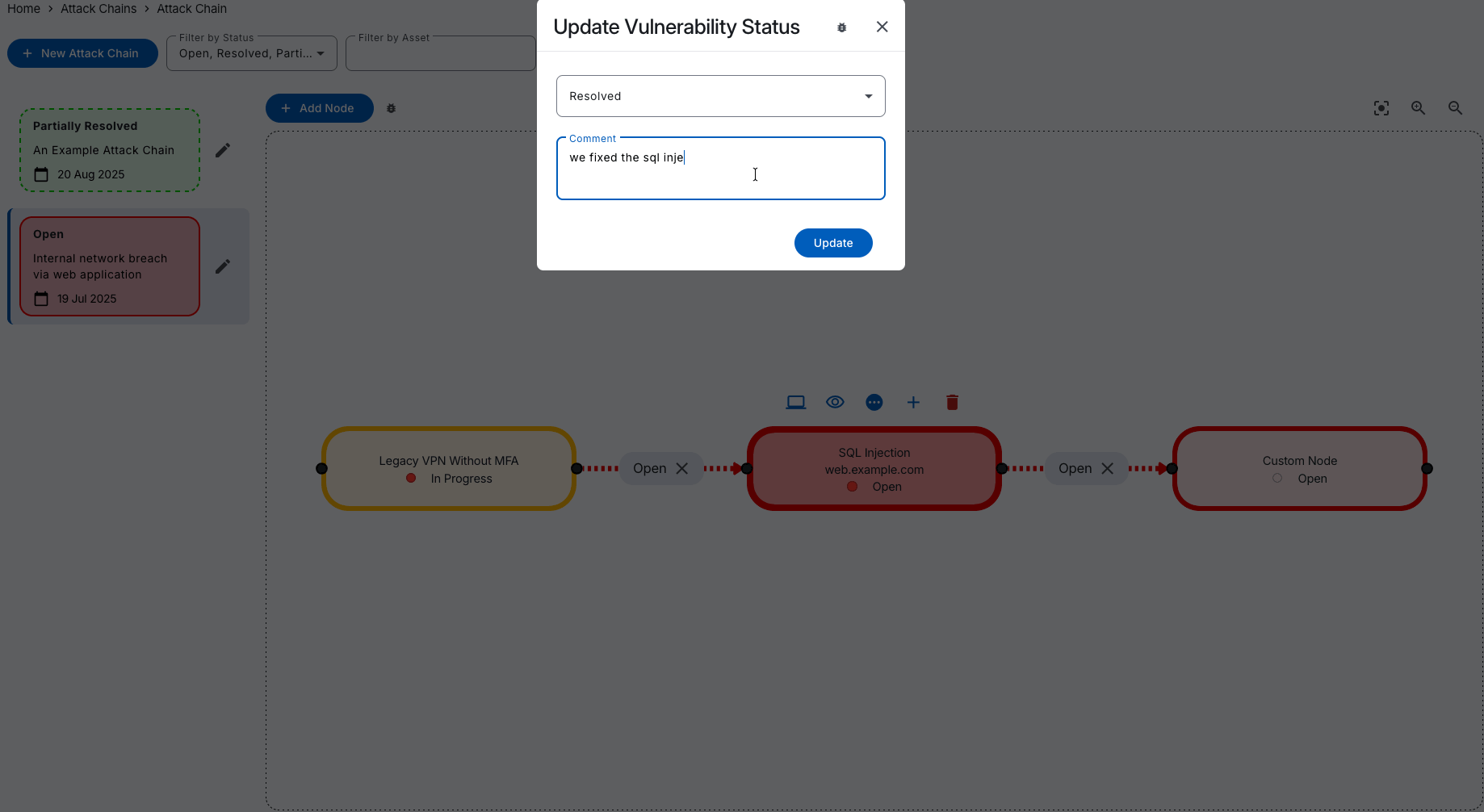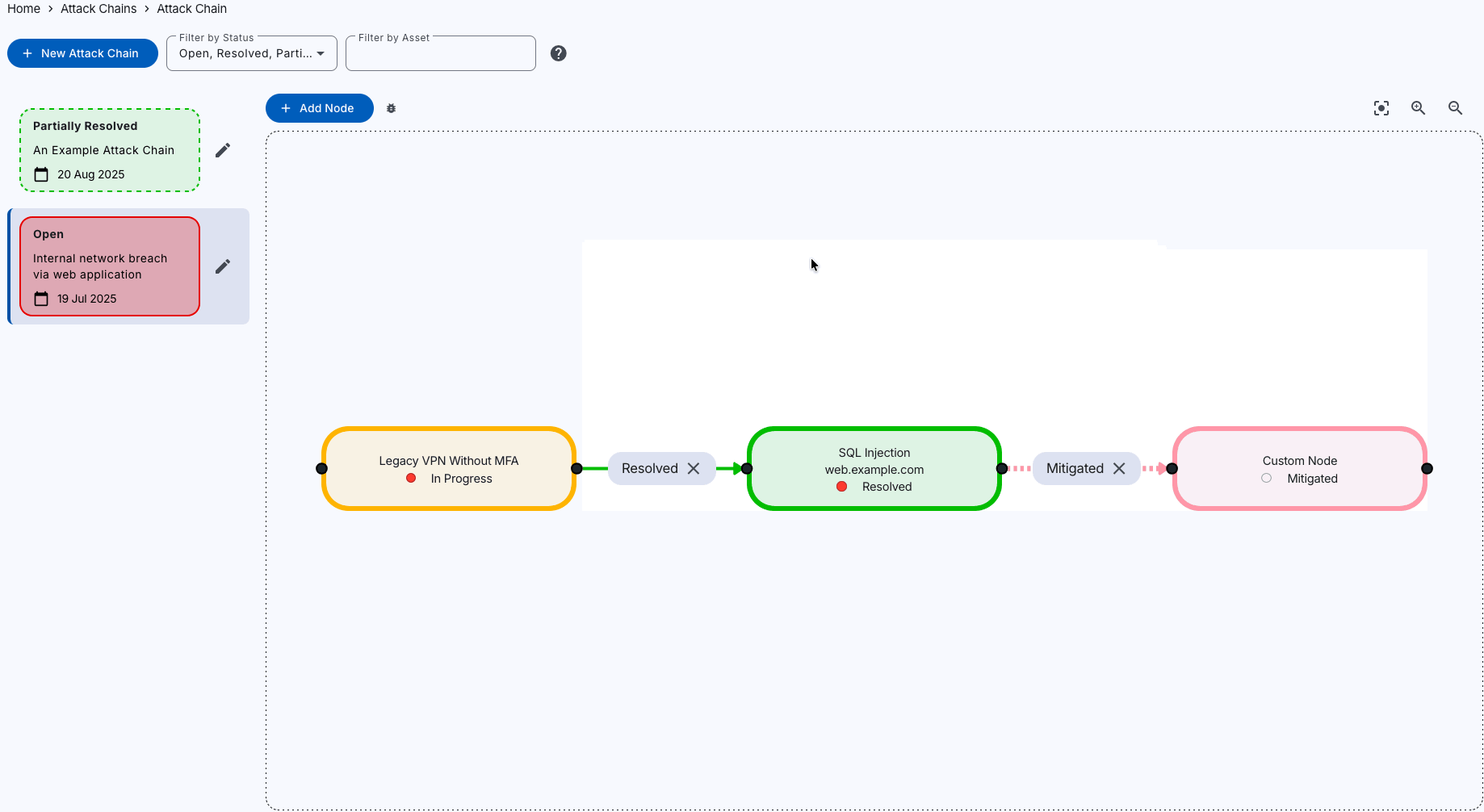
Visualise the Cyber Kill Chain
Understand the route to compromise to better anticipate and block real-world attack paths.
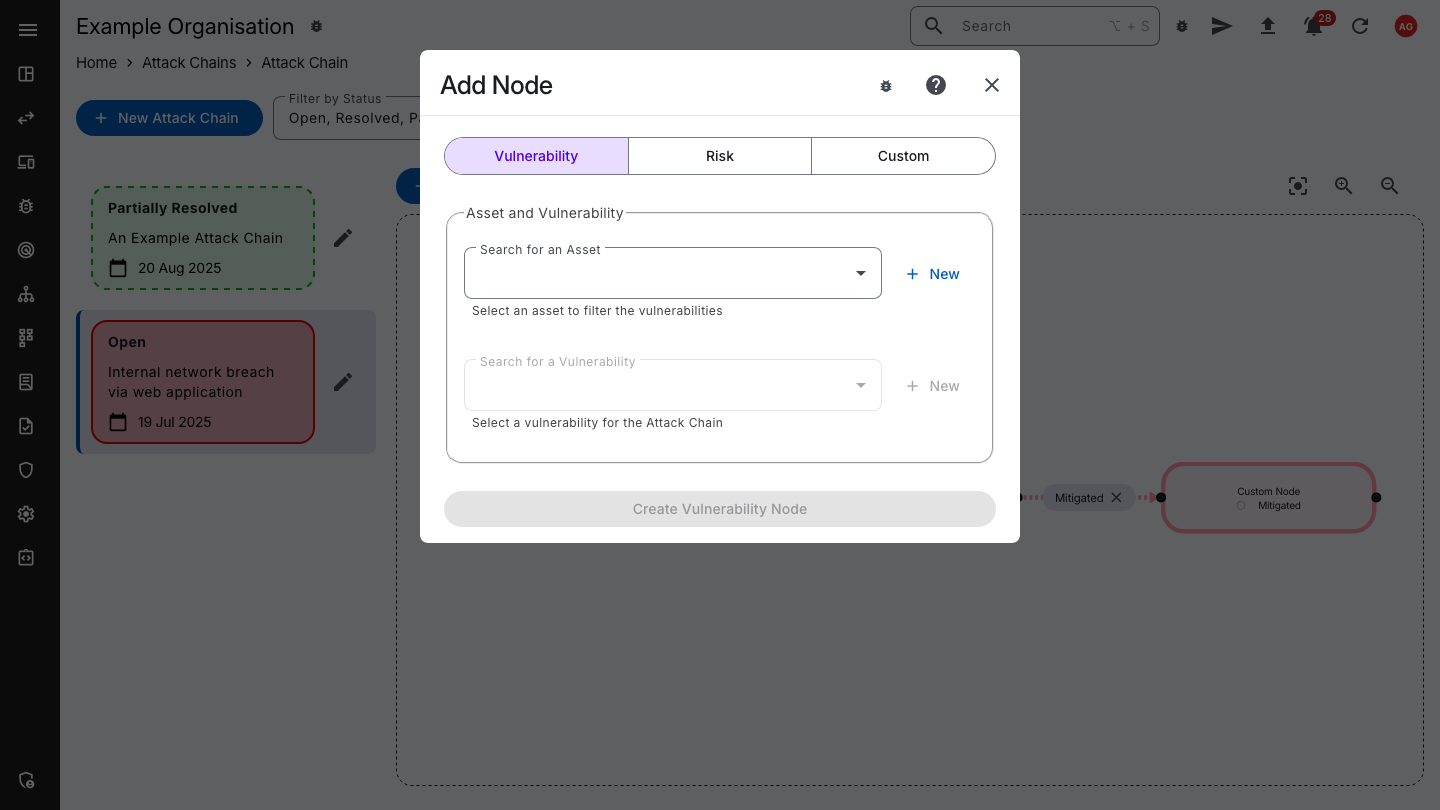
Our Attack Chain mapping feature offers dynamic network flow graphs to visualise your attack paths, helping you understand relationships between assets and vulnerabilities, and collaborate with your team.