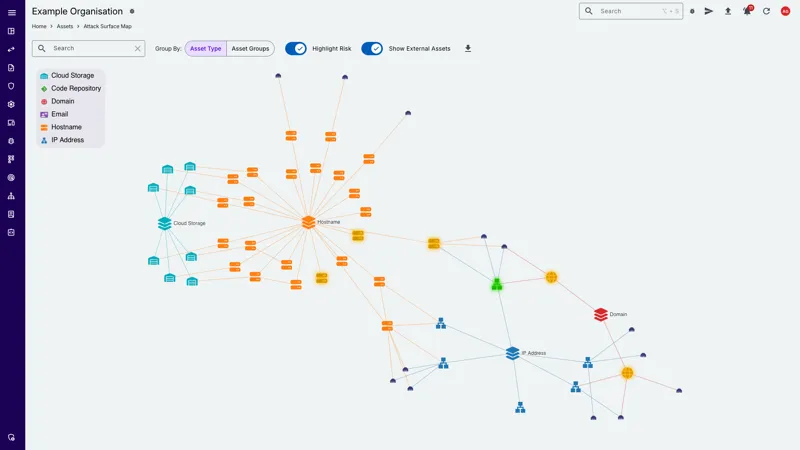
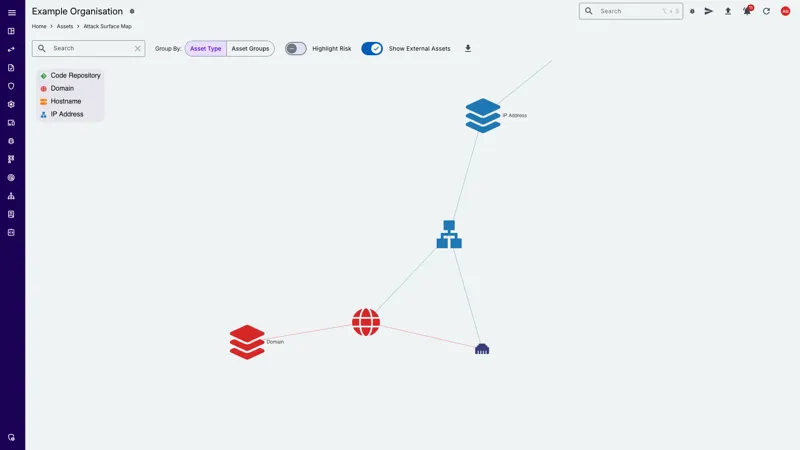
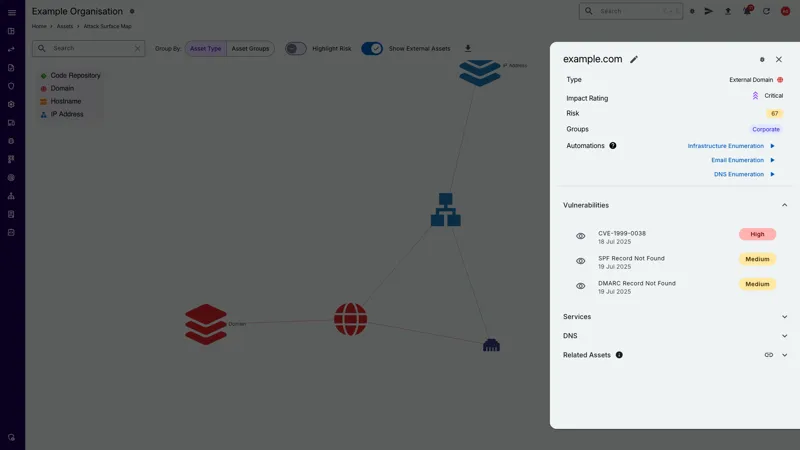
Interactive Attack Surface Map
Visualise Your Attack Surface
Interactive visualisation of your attack surface to understand the relationships between assets, services, and risk.
Our Attack Surface Map feature provides a dynamic map that shows the relationships between assets, vulnerabilities, services and risk, providing a clear picture of your security posture.