Vulnerability Scanning
Automate Your Vulnerability Scanning
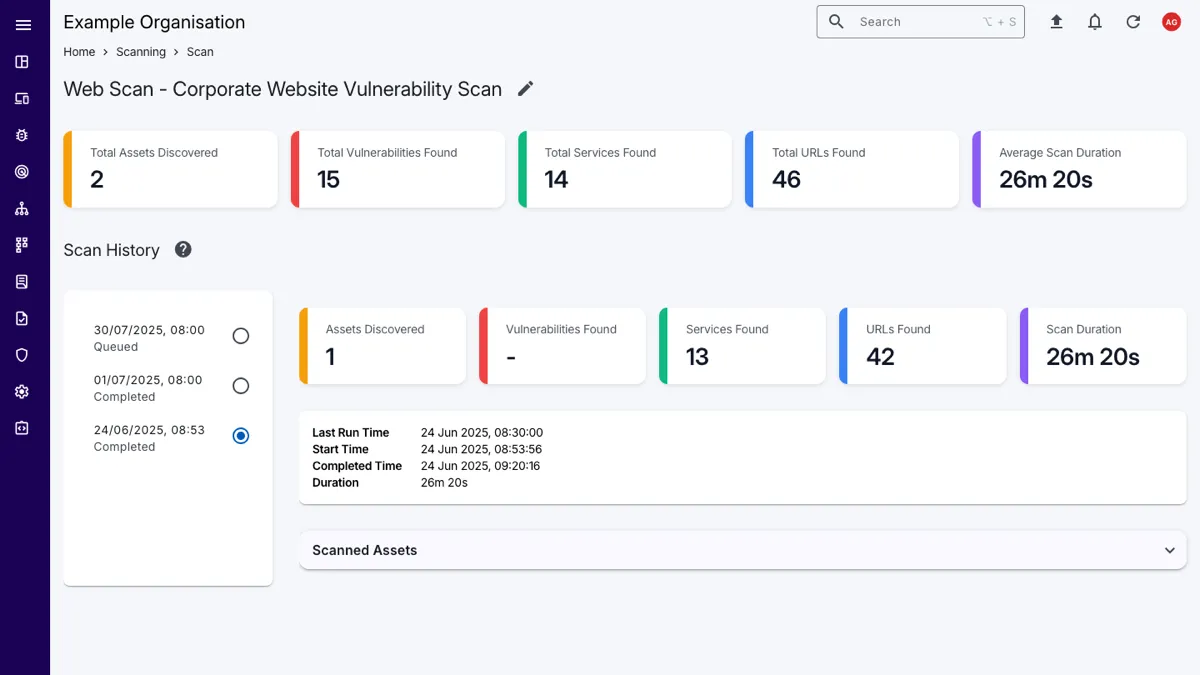
Our platform provides an integrated solution for asset discovery, port scanning, and vulnerability scanning, allowing you to keep an eye on your attack surface.
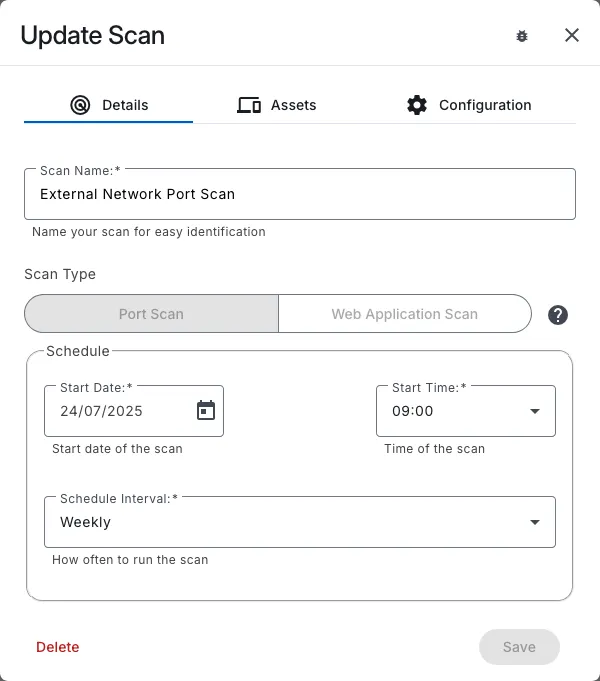
With scheduled scanning, you can ensure that your assets are regularly scanned for vulnerabilities and exposed services, so you can easily track and manage vulnerabilities across your environment.