External Network Security
External network security focuses on protecting the systems and services that are exposed and accessible from the internet. This includes firewalls, network gateways, remote access services, and any infrastructure that forms your organisation’s external attack surface.
Because these systems are publicly reachable, they are continuously probed by attackers looking for misconfigurations, exposed services, and known vulnerabilities. A single weakness on the perimeter can provide an entry point into internal systems or sensitive data.
External network penetration testing simulates real-world attacks against your internet-facing infrastructure to identify what an attacker could discover and actually exploit. The goal is not just to find vulnerabilities, but to understand exposure, validate risk, and prioritise remediation based on real impact.
Who Needs External Penetration Testing?
External network testing is essential for:
Regular testing helps meet compliance requirements and validates that your external security controls are working as intended.
What We Test
Our perimeter network penetration testing service focuses on your external assets, including:
Common External Network Vulnerabilities
Our testing frequently identifies:
Pricing
Pricing depends on the size of your external footprint, number of IPs, exposed services and cloud complexity. A fixed price is confirmed after a short scoping review.
Why Choose Exploitr
Our penetration testing services are designed to uncover real, exploitable risks and provide organisations with clear guidance on how to fix them.
Manual, consultant-led testing
Real security experts, not just automated tools. Get thorough analysis from experienced professionals.
Remediation advice tailored to you
Specific guidance for your business and tech stack with practical, actionable recommendations.
Standards-led testing methodology
Testing delivered with industry best practices and testing methodologies.
Direct communication
Talk directly with experienced testers throughout the engagement process.
Real-world threat testing
Testing aligned to actual attack patterns that matter to your business.
Transparent, fixed pricing
Know your costs upfront with transparent, fixed-price proposals.
Get the right level of testing
What Our External Testing Includes
External penetration testing involves an assessment of your organisation’s internet-facing infrastructure. This type of testing is crucial for identifying vulnerabilities that could be exploited by attackers who are attempting to gain initial access to your systems from the outside.
Asset Discovery and Enumeration
To achieve this we use a combination of automated tools and manual techniques to ensure the breadth and depth of coverage you deserve.
Vulnerability Detection and Analysis
This includes identifying outdated software, misconfiguration, and other common security issues that could be exploited by attackers.
Exploitation and Lateral Movement
All exploitation is performed with appropriate safeguards and can be limited based on your risk tolerance
Manual Testing
With each service we identify the version of the software and perform further analysis to identify vulnerabilities and potential exploits.
Unauthorised Access
Through this we can determine if there are any weaknesses with brute force mitigation controls.
Detailed Reporting
Our reports are tailored to both technical and non-technical stakeholders, ensuring clarity and understanding.
Ready to Test Your External Security?
No obligation. No sales pressure. Just transparent pricing and expert guidance.
Communicate with our testers directly
Experts in providing thorough testing coverage
Professional services you can trust
Fixed pricing with no surprises
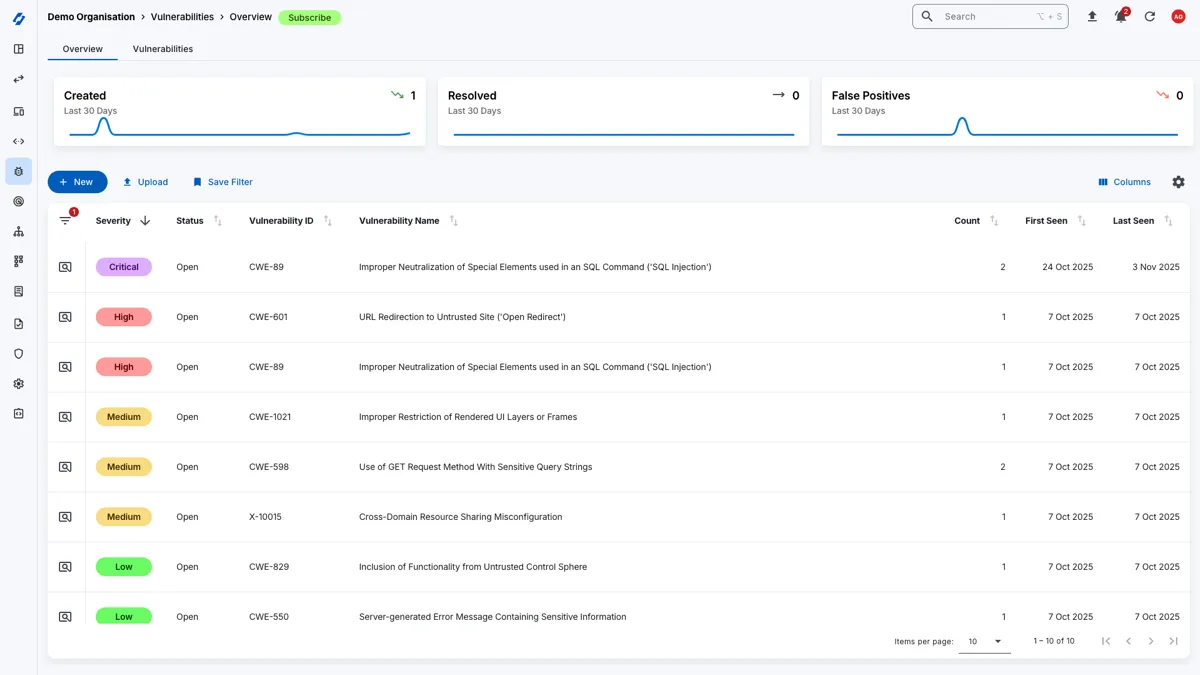
Attack Surface Management
Gain complementary access to the Attack Surface Center platform with your penetration test to manage your vulnerabilities, assets, and track remediation progress.
The time taken for typical external penetration tests depends on scope, with the average test taking between 3-5 days. Reports are delivered within 2 business days of testing completion.
External testing is non-disruptive and designed to safely simulate real attacks without causing service outages. We coordinate timing and agree acceptable testing windows. However, there is an element of risk for any form of penetration testing, network, or vulnerability scanning – we will enquire as to any legacy, sensitive or business critical services during scoping to ensure that extra care is taken to minimise any potential impact.
Modern day security testing shouldn’t be treated as a once per-year activity. We recommend annual testing at an absolute minimum, with additional testing after significant infrastructure changes, new service deployments, or following any security incidents.
External testing focuses on internet-facing systems accessible to any attacker, while internal testing assumes an attacker has already gained access to your internal network.
Yes, our external testing includes cloud-hosted infrastructure on AWS, Azure, GCP and other platforms that form part of your external attack surface.
Yes, external testing can typically be performed during business hours as it simulates attacks that occur constantly against internet-facing systems.

