Internal Network Security
Internal network security focuses on protecting systems, users, and data after initial access has been obtained. This reflects how most real-world breaches occur, where attackers gain a foothold through phishing, stolen credentials, or a service exposed to the internet – then move laterally within the internal environment.
Internal networks often contain critical assets such as Active Directory, file servers, databases, and other administrative systems. Weak access controls, misconfigurations, or excessive privileges can allow an attacker to escalate access and compromise large parts of the organisation.
Internal network penetration testing simulates a realistic breach scenario – assuming an attacker has already gained initial access through phishing, compromised credentials, or an external vulnerability. We then evaluate how far they could progress inside your environment.
Our testing identifies privilege escalation paths, lateral movement opportunities, and access to critical systems like domain controllers, databases, and file servers. This approach helps you prioritise remediation efforts where they’ll have the greatest impact on reducing real-world breach risk.
Who Needs Internal Network Pentesting?
External network testing is essential for:
Regular internal testing validates that security controls limit lateral movement and prevent attackers from accessing your most critical assets.
Why Choose Exploitr
Our penetration testing services are designed to uncover real, exploitable risks and provide organisations with clear guidance on how to fix them.
Manual, consultant-led testing
Real security experts, not just automated tools. Get thorough analysis from experienced professionals.
Remediation advice tailored to you
Specific guidance for your business and tech stack with practical, actionable recommendations.
Standards-led testing methodology
Testing delivered with industry best practices and testing methodologies.
Direct communication
Talk directly with experienced testers throughout the engagement process.
Real-world threat testing
Testing aligned to actual attack patterns that matter to your business.
Transparent, fixed pricing
Know your costs upfront with transparent, fixed-price proposals.
Get the right level of testing
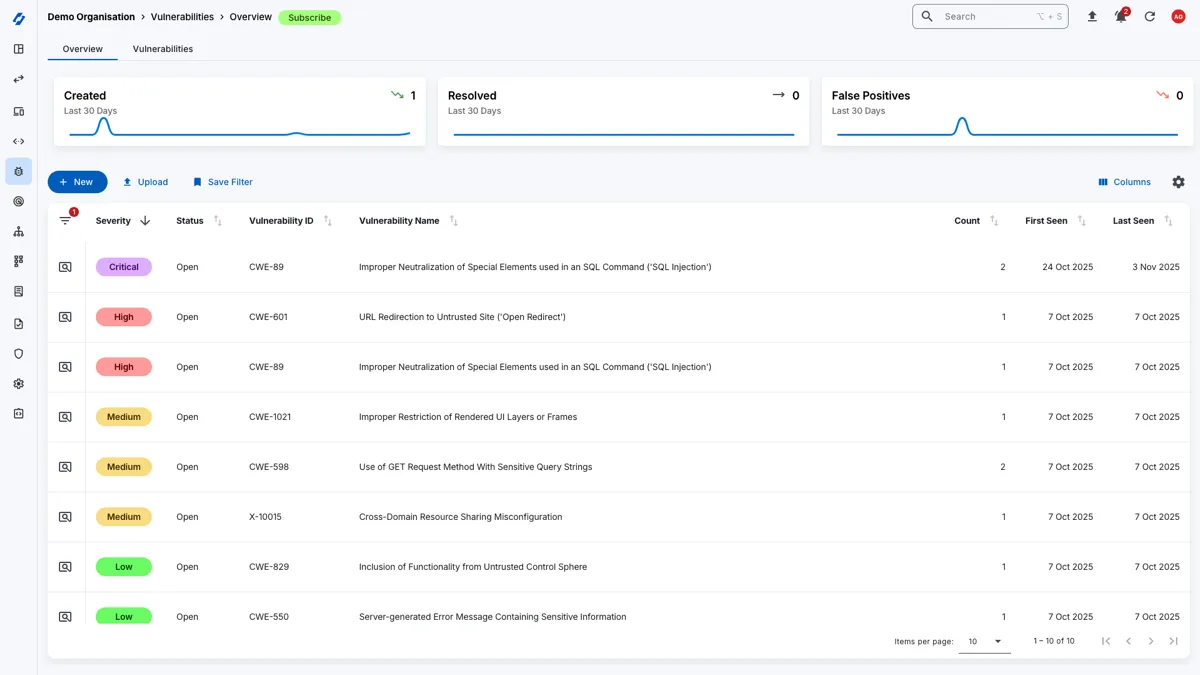
How We Conduct Internal Network Testing
Internal network penetration testing involves an assessment of your organisation’s internal network’s servers, network devices, and workstations.
This type of testing is crucial for identifying vulnerabilities that could be exploited by attackers who have already gained access to your internal network, whether through phishing, social engineering, or other means.
Reconnaissance & Enumeration
Credential Attacks & Harvesting
Exploitation & Privilege Escalation
Lateral Movement Simulation
Impact Assessment & Reporting
provide risk-rated technical analysis, and deliver actionable remediation guidance for your IT and security teams.
Pricing
Pricing depends on network size, number of workstations and servers, domain complexity and testing depth. A fixed price is confirmed after a short scoping review.
What We Test
We go beyond basic network scanning to identify real attack paths that could lead to complete network compromise.
Active Directory Security
Domain controllers, GPO misconfiguration, Kerberos weaknesses, privileged group memberships, trust relationships, and AD certificate services vulnerabilities.
Internal Network Segmentation
VLAN isolation, firewall rules between network zones, access controls preventing lateral movement, and segregation of critical systems.
Exploitation & Privilege Escalation
Local privilege escalation on workstations and servers, service account abuse, kernel exploits, and misconfigured permissions allowing unauthorised elevation.
Password Security & Credential Reuse
Password spraying attacks, credential stuffing, hash cracking, identification of weak or default passwords across the network.
Endpoint & Server Configurations
Windows workstations and servers, unpatched systems, insecure services, weak local administrator passwords, and endpoint security controls.
Lateral Movement Techniques
Pass-the-hash attacks, token impersonation, SMB relay attacks, and exploitation of trust relationships between systems.
Access to Sensitive Systems
File servers containing intellectual property, database servers with customer data, backup systems, and administrative consoles.
Legacy Protocols & Misconfigurations
LLMNR/NBT-NS poisoning, SMBv1 vulnerabilities, insecure protocols, and outdated network services that facilitate attacks.
Network Devices & Internal Firewalls
Switches, routers, internal firewalls, wireless access points, and network infrastructure that could be compromised or misconfigured.
Assumed Breach Testing
We start from the position that an attacker has already gained initial access (through phishing, stolen credentials, or a compromised device). This realistic scenario lets us focus on what matters most: how far they could get once inside.
Ready to Test Your Internal Network Security?
Communicate with our testers directly
Experts in providing thorough testing coverage
Professional services you can trust
Fixed pricing with no surprises
Attack Surface Management
Gain complementary access to the Attack Surface Center platform with your penetration test to manage your vulnerabilities, assets, and track remediation progress.