Web Application Security
Web application security focuses on protecting the systems that power modern websites, platforms, and online services. These applications often handle sensitive data, business logic, and user interactions – making them a frequent target for attackers.
Security weaknesses often arise from insecure code or third-party libraries that can affect application logic, authentication flows, and how users interact with the system. These issues are rarely detected by automated scanners.
Web application security testing aims to identify vulnerabilities that could allow an attacker to access data, bypass controls, or abuse functionality. By simulating real-world attack techniques, penetration testing helps organisations understand their true exposure and to prioritise remediation based on business risk and impact.
This type of testing is particularly important for applications exposed to the internet or used by customers, partners, or internal staff.
Who Needs Web Application Penetration Testing?
Web application testing is essential for:
Regular penetration testing validates your security controls, helps meet compliance requirements, and protects your reputation by identifying vulnerabilities before they can be exploited.
What We Test
We go above and beyond the OWASP Top 10 to ensure that your applications are secure against a wide range of threats.
Assess the security of your web applications, websites, and APIs. Identify security vulnerabilities and demonstrate exploitation to discover the potential impact of a successful attack.
Authentication & Authorisation
Multi-factor authentication bypass, password policy weaknesses, session fixation, privilege escalation, and insecure direct object references (IDOR).
Injection Vulnerabilities
SQL injection, command injection, LDAP injection, XML injection, and server-side template injection across all input vectors.
Business Logic Flaws
Race conditions, workflow bypass, price manipulation, payment logic abuse, and application-specific logic vulnerabilities that automated scanners miss.
Session Management
Session hijacking, cookie security, token handling, timeout configurations, and cross-site request forgery (CSRF) protections.
Data Exposure
Sensitive data in URLs, error messages, source code comments, and insecure data transmission or storage.
API Security
REST and GraphQL API testing, rate limiting, authentication mechanisms, data validation, and API-specific vulnerabilities (OWASP API Top 10).
File Upload & Handling
Unrestricted file uploads, path traversal, arbitrary file access, and server-side vulnerabilities through file processing.
Client-Side Security
Cross-site scripting (XSS), DOM-based vulnerabilities, insecure JavaScript libraries, and client-side logic manipulation.
Access Control
Horizontal and vertical privilege escalation, forced browsing, missing function-level access controls, and role-based access bypass.
Additional Security Assessments
Source Code Review
Manual review of application source code to identify security vulnerabilities, insecure coding patterns, and logic flaws that may not be detectable through black-box testing alone. Particularly valuable for pre-release security validation or high-risk applications.
Infrastructure & Configuration
Security headers, TLS/SSL configuration, subdomain takeover risks, and server misconfigurations that impact application security.
Our Testing Approach
Manual-First Testing Methodology
While we use automated tools for discovery and efficiency, every finding is manually validated and exploited by our consultants. We focus on business logic flaws, complex authentication bypasses, and chained vulnerabilities that automated scanners cannot detect.
Real-World Attack Simulation
We think like attackers by combining vulnerabilities, testing business logic, and exploring unconventional attack paths. Our goal is to demonstrate actual risk, not just report theoretical vulnerabilities.
Authenticated & Unauthenticated Testing
We test both as an anonymous attacker and as authenticated users across different privilege levels (standard user, admin, etc.) to identify privilege escalation and access control issues.
Framework & Platform Coverage
Testing includes both traditional web interfaces and modern architectures: single-page applications (SPAs), progressive web apps (PWAs), API-driven applications, and microservices architectures.
Pricing
Pricing depends on application complexity, supported platforms, authentication mechanisms, and integration with external services. A fixed price is confirmed after a short scoping review.
Common Vulnerabilities We Identify
Our testing regularly uncovers critical security issues that put applications at risk:
Broken Authentication
Weak password policies, insecure session management, missing MFA enforcement, and authentication bypass vulnerabilities that allow unauthorised access.
Injection Flaws
SQL injection allowing database access, command injection enabling server compromise, and other injection vulnerabilities across input validation points.
Broken Access Control
Insecure direct object references (IDOR) allowing access to other users’ data, missing function-level access controls, and privilege escalation vulnerabilities.
Business Logic Vulnerabilities
Payment manipulation, workflow bypass, race conditions, and application-specific flaws that automated tools cannot detect.
API Security Issues
Missing rate limiting, broken object-level authorisation, mass assignment vulnerabilities, and API-specific weaknesses.
Sensitive Data Exposure
Unencrypted data transmission, sensitive information in error messages, insecure encryption, and data leakage through various channels.
Early detection through penetration testing allows your team to remediate these issues before they can be exploited by attackers.
Why Choose Exploitr
Manual testing, not scans
Clear reporting and advice
Certified testing team
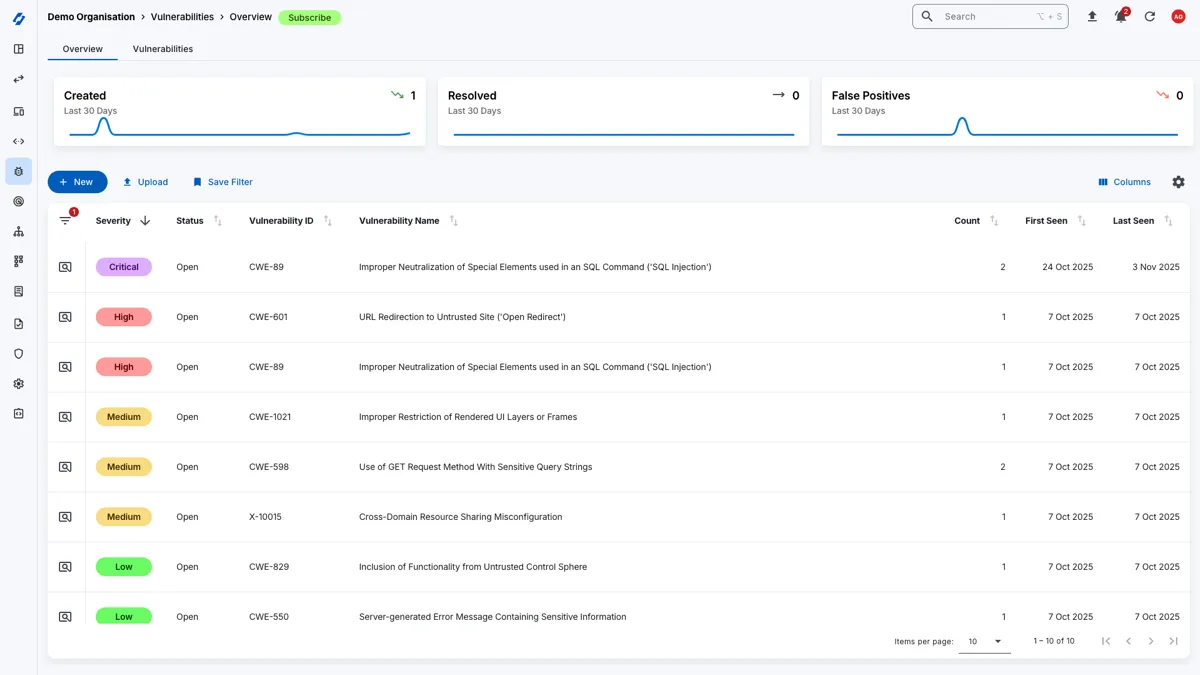
Attack Surface Management
Gain complementary access to the Attack Surface Center platform with your penetration test to manage your vulnerabilities, assets, and track remediation progress.
Ready to Secure Your Web Applications?
Most web application tests take 3-7 days depending on scope and complexity. Testing can be performed for your development, staging, or production environments. Reports are delivered within 2 business days of testing completion.
There is an inherent risk with penetration testing – we use safe testing techniques and coordinate with your team to minimise any potential impact. Testing is typically performed in non-production environments, though production testing can be conducted with appropriate safeguards.
Yes, API testing is included when APIs are part of the application’s functionality. The web application penetration test is usually scoped based upon the functionality of the application and not the number of API endpoints that are exposed.
For API-only applications, we offer dedicated API penetration testing.
Yes, we regularly test React, Angular, Vue applications and other modern frameworks, including their API backends and client-side logic.
We recommend annual testing at minimum, with additional testing after major releases or breaking changes, significant feature additions, or architectural changes. Many organisations may benefit from continuous testing through our Pentest as a Service offering.
Yes, complimentary focused retesting is included to verify that identified vulnerabilities have been properly remediated. To conduct this type of testing we would require the same level of access to the application and any relevant user roles to repeat the assessment.
As part of our standard operations within Exploitr, we also provide details and repeatable evidence as part of our assessment reports – so your team can validate and verify remediation internally.
Yes, we offer source code review as a complementary service to penetration testing.
Code reviews can identify vulnerabilities in the development phase and provides additional assurance beyond black-box testing. We typically call this “open-book” testing.
Contact us to discuss adding a code review to your engagement.
Yes, we can test the server-side components and APIs that mobile applications interact with. For a more dedicated mobile application assessment, consider pairing with mobile application testing.

